Posts Tagged ‘cyber harassment’
Men’s Cyber Abuse Against Intimate Female Partners / Speak Out Loud- CLARE MURPHY PHD
This article was originally posted on Speak Out Loud ( link below) by one of PMA International’s esteemed leaders- Clare Murphy PHD
Please note; although this article is specific to Men’s cyber abuse towards a female partner, cyber abuse perpetrators are of both genders. Cyber abuse also occurs from individuals who have a variety of relationship dynamics with their target- IE; co workers, colleagues in business and organizations, family members ect. Cyber abuse between any relationship dynamic and gender is clearly abuse and should be labeled and dealt with as such.
http://speakoutloud.net/intimate-partner-abuse/cyber-bullying
Before the proliferation of Cyber Abuse, it was often possible for women to create a safe distance from their abuser —But Cyber Abuse Closes that Gap — There is no longer such a thing as a safe distance from Coercive Control.
The invention of the internet and the development of electronic and digital forms of communication technology have changed the lives of millions of people in good ways and bad ways. Perpetrators of intimate partner abuse have a whole new arsenal of ammunition to use to establish and maintain power and control over their partners. A wide range of electronic devices including mobile phones, mobile phone cameras, video recorders and other technologies are used to tease, harass, mock, torment, monitor, stalk, intimidate, and coercively control their partner. Perpetrators use social media, emails, text messages, chat rooms, tweets, websites and other internet technologies too.
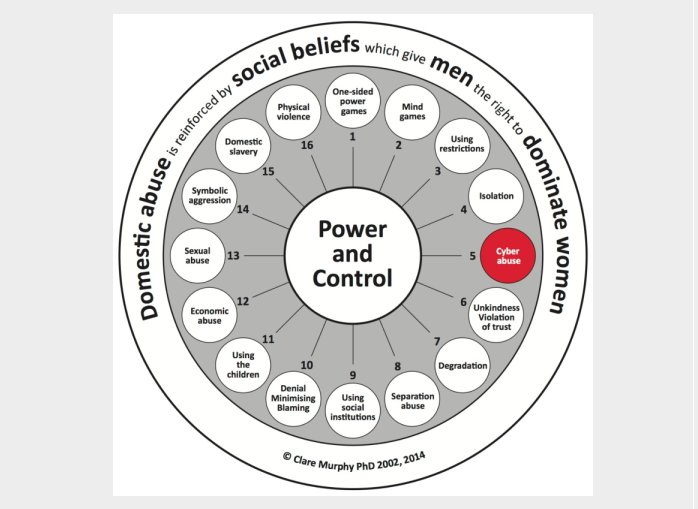
I’m writing this blog post to introduce you to a slight change to my power and control wheel. If you look at circle #5 above you’ll see I’ve renamed it Cyber Abuse.
(The list of tactics relating to the previous title in that circle was Over protection and ‘caring’. I’ve integrated that list of coercive control tactics within relevant categories in my updated long list of tactics here.)
Cyber Abuse was not talked about when I first interviewed women who had been psychologically controlled by their male partners. Nearly 13 years later, Online Social Cruelty, Cyberbullying and Cyberstalking are commonly used by men against female partners – both within the relationship and after separation.
Online Social Cruelty
An extensive range of Online Social Cruelty used by men against current or ex-partners includes putting her private phone number and other personal details for sale Online, and impersonating her Online by using her screen name or password.
Some men spread derogatory messages, false rumours and confidential material to embarrass, humiliate and defame their partner. Others tell their partner who she can and cannot ‘friend’ or ‘follow’ on social media, or he may use his MySpace, Facebook status, and other Social Media to write degrading statements about her. These tactics are intended to damage her self image.
Some men are known to create Website/Online forums such as chat rooms or twitter accounts to write abusive messages about her, and those close to her, and he may also send unwelcome messages directly to her friends, family, and employer.
Sexting is an Online form of men’s intimate partner sexual abuse that entails creating and posting non-professional sexual or nude images or videos of her on social media. Sexting is an unwelcome and significantly damaging form of abuse.
Men who belittle and humiliate their partner Online are exposing her to gigantic audiences, therefore forcing her to experience overwhelming vulnerability. These invasive tactics purposefully steal women’s sense of privacy and security.
Cyberbullying
Many men who coercively control their female partners engage in repeated forms of Cyberbullying. This includes stealing or forcing her to disclose passwords, insisting that she always be available at the end of the phone, and demanding that she take nude photos of herself and send them to him.
Some men use recordings, photos and videos to blackmail their partner or ex-partner, and may record violent and sexual assaults followed by threats to post them Online. Other cyberbullying tactics include coercing her to ‘volunteer’ her phone for him to check, and manipulating or intimidating her if she delays responding to his text messages. He may send unwanted threatening and abusive emails, tamper with her emails, and check for the content of her ‘sent’ and ‘deleted’ folders.
I’ve had clients whose partner emailed computer viruses to her and who engaged in Spamming by purposefully flooding her email box with junk mail. Other men engage in Mail Bombing by sending lengthy or sizeable emails that use all her computer memory.
Cyberbullying also includes telling her who she can and can’t ‘friend’ on social media, threatening to, or actually uploading and distributing personal photos and videos without her consent.
The lines are blurred between Offline bullying and Cyberbullying. Bullying is anxiety-creating no matter what form it takes. Some women are able to escape Offline bullying, but there is less ability to escape from bullying in Cyberspace.
This is particularly the case for women with disabilities who experience the debilitating effects of Cyberbullying. Men who have a partner whose mobility, speech, hearing or sight is impaired may sabotage or remove her electronic and communication aids, interfere with her ability to use her TRS, sabotage or remove her braille equipment.
Cyberstalking
Digital Voyeurism is a form of Cyberstalking that some men use to control their partner or ex-partner. Cyberstalking entails using a range of technology to monitor her, by for example tapping her phoneline, installing hidden surveillance cameras and listening devices in her house, or accessing her internet banking to monitor, or use, her funds.
Men in relationship with women who are hearing impaired may stalk their partner by reviewing the history on her TDD and TTY phone device message delivery services.
Other forms of Cyberstalking include willfully sending her excessive amounts of unwelcome texts, phone calls and voice messages, frequently looking through her phone checking her contacts, calls, texts, voice messages and photos. Some men make malicious use of GPS to track her movements. Other men will use her caller ID on her phone to pursue her and track her down.
Cyberstalking includes Doxxing
Doxxing entails trawling through the internet to locate every type of personal information pertaining to her, such as her contact details, geographical location, and passwords. Some men follow and monitor their partner’s Online movements, or sign into her Social Media accounts, chat forums and her other Social Network sites.
Installs computer software to stalk her
Abusers use Spyware and Sniffer Programmes to detect information such as usernames and passwords that are sent or received on her computer. Spyware records all her attempts to delete emails and her internet browser history. Installation can be achieved by direct access to her computer or by concealing it in an email attachment.
Installs computer hardware to stalk her
Abusers install Keystroke Logging Hardware onto her keyboard, or the back of her computer to keep tabs on who she communicates with, and where, or if, she seeks support or advice for the abuse and control she’s experiencing.
Anyone can install software and hardware for malicious reasons, they do not need to have computer expertise to make such installations.
Any form of Cyberstalking Causes Significant Damage
In a research project of women’s experiences of Protection Orders, one woman said:
“I never went to the police about these communications as invariably he would make sure to put something of a defamatory or insulting nature about me and I wondered if they would believe his interpretation of things rather than my own.” Pg 204(1)
This woman went to the police again and, “and fortunately for once, I got a constable who actually listened to me.” Pg 204(1)
Unfortunately though, in most countries non-physical tactics of coercive control are considered minor by legal establishments, however, coercive control, no matter what form it takes, is debilitating, destabilising and can lead to a deadly outcome. Read this blog post about how to keep yourself safe if you believe your partner could kill you. And read this post if you are planning to leave.
Stalking a current or ex-intimate partner Offline often involves threats of danger, or actual danger. The same is true of Cyberstalking.
Cyberstalking can lead to dangerous outcomes.
One research project exploring the use of “stalking with technology”(2) noted that:
“While hiding from an abusive partner, a woman needed to get papers to her abuser. She sent them to him via her attorney from the shelter’s fax machine. Her attorney faxed the papers to the abuser’s attorney, who gave the papers to the abuser.” Pg 845(2)
This was highly dangerous activity on the part of both attorneys because “The abuser got the phone number and location of the victim” Pg 845(2) as it was printed on the fax paper.
Other studies(4) find frustration with the minimal accountability and justice. Professionals dealing with any form of intimate partner stalking must take every seemingly isolated minor incident seriously because behind that one incident is a backlog of multiple forms of Coercive Control. Coercive Control is one of the major risk factors that leads to physical violence against female partners and to murdering women and their children.
Cyber Abuse of any kind leads to Long Term Negative Impacts
When a man engages in an ongoing systematic pattern of Offline abuse, control and stalking it is highly likely he will also engage in an intrusive systematic pattern of Online Social Cruelty, CyberBullying and CyberStalking. The intertwining of all this can lead to crazymaking, severe anxiety, panic attacks, thoughts of suicide. The long term negative impacts can be palpable for women and the children exposed to such abuse.
Some CyberSafety Tips
1 Change your usernames and passwords
2 Block your caller ID on your Phone
3 Turn off GPS location facilities on your computer, camera and Phone
4 Use a safe email address – perhaps create a new one
5 Use a safe computer, perhaps at the library or someone you know who your abuser does not know
6 Delete your internet history (although digital footprints can never be entirely deleted)
7 Keep a record of all forms of abuse (ensure that record is kept safe from the abuser)
These are basic safety measures if you are being harassed. However if you are in danger there are many more measures you may need to take to stay safe in relation to communication technologies and CyberSpace. Here are three documents compiled by researchers that you could use for taking stronger safety measures . . . . These tips from Women’s Legal Services, NSW — And these ones by Web Wise Women — Also these Technology Safety Quick Tips from the National Network to End Domestic Violence.
References:
Robertson, Neville, Busch, Ruth, D’Souza, Radha, Lam Sheung, Fiona, Anand, Reynu, Balzer, Roma, . . . Paina, Dulcie. (2007). Living at the cutting edge: Women’s experience of Protection Orders: Volume 2: What’s to be done? A critical analysis of statutory and practice approaches to domestic violence.
Southworth, Cynthia, Finn, Jerry, Dawson, Shawndell, Fraser, Cynthia, and Tucker, Sarah. (2007). Intimate partner violence, technology, and stalking. Violence Against Women, 13(8), 842-856.
Hand, Tammy, Chung, Donna, and Peters, Margaret. (2009). The use of information and communication technologies to coerce and control in domestic volence and following separation Stakeholder Paper 6: Australian Domestic and Family Violence Clearinghouse.
West, Jessica. (2014). Cyber-Violence Against Women. Vancouver, BC: Battered Women’s Support Services: The Violence Stops Here.
Written by protectivemothersallianceinternational
November 27, 2014 at 11:24 pm
BILL WINDSOR OF LAWLESS AMERICA PUTS CLAUDINE DOMBROWSKI AND THE AMERICAN MOTHERS POLITICAL PARTY OUT OF THE STALKING AND THREAT BUSINESS.
 See on Scoop.it – The War Against Mothers
See on Scoop.it – The War Against Mothers
BILL WINDSOR OF LAWLESS AMERICA PUTS CLAUDINE DOMBROWSKI AND THE AMERICAN MOTHERS POLITICAL PARTY OUT OF THE STALKING AND THREAT BUSINESS.
I haven’t wanted to telegraph my visit to the Shawnee County Courthouse in Topeka Kansas today. Today was the trial of Claudine Dombrowski on stalking charges. Case 13D-1747.
Claudine Dombrowski has been ordered to post nothing about me and remove all postings in regard to me. I doubt that Claudine Dombrowski can comply with the order, so I believe she is destined for criminal charges and contempt charges.
If she has a weapon, I believe she is restricted and may lose it. She could also be prosecuted for interstate travel to commit stalking or violence and interstate stalking.
There was another Claudine Dombrowski victim at the trial, and she is even happier than I am. Others will likely be following with actions similar to mine. Since Claudine Dombrowski IS the American Mothers Political Party, it seems to me that their Facebook pages and web pages will have to disappear. I hereby advise them to make copies of everything they remove as these are subject to subpoena in both civil and criminal matters that are pending. All the Muthas must heed this requirement, or they could be found guilty of the crime of destroying evidence.
I think I’m going to find a piece of pie.
William M. Windsor
nobodies@att.net
Here’s to you Bill with L.O.V.E PMA INTL.
Written by protectivemothersallianceinternational
September 13, 2013 at 12:56 am
Posted in child abuse, children, children's rights, domestic violence, family court abuse, family court corruption, famly law
Tagged with @angelfury1212, abuse, American Mothers Political Party, AMPP, angelfury, Barry Goldstein, Battered Mothers Custody Conference, Bill Windsor, BMCC, California Protective Parents, California Protective Parents Association, Center for Judicial Excellence, child custody, children's rights, CJE, Claudine Dombrowski, Connie Valentine, corruption, court corruption, CPPA, crime, Cyber bullying, Cyber crimes, cyber harassment, Cyber stalking, divorce, domestic violence, domestic violence women's issues, family court, family court abuse, family court corruption, family law, human rights, Janice Levinson, Jennifer Collins, Kathleen Russell, Lawless America, Lundy Bancroft, Mo Hannah, MOLC, mother's rights, mothers, Mothers of Lost Children, NSCC, Occupy, PMA, PMA INTERNATIONAL, protective mother, Protective Mothers Alliance International, Tammy Stefano, The National Safe Child Coalition, Topeka Kansas, women's issues
Lundy Bancroft Takes a Strong Stand Against Abusers Within The Mothers’ Movement
http://lundybancroft.blogspot.com/
Thank you Lundy!. We love and support you back!
Please Read; IMPORTANT MESSAGE FROM LUNDY
Defending A Women’s Rights Activist Who Is Under Attack
NOTE: This post is about some of the internal dynamics of the national movement fighting for the custody rights of abused women (also referred to as “protective mothers,” because they are in the position of needing to protect their children from the other parent, but family courts are not permitting them to do so). If this issue doesn’t interest or affect you, or if you get triggered by news about infighting, I encourage you to skip this post. But for those of you who are involved in the custody issue, it’s important to know about the attacks on activists that are happening.
For over a decade I have been one of the leaders in the international effort to secure full human rights for protective mothers and their children. There is no cause that remains as close to my heart day in and day out.
I am writing in response to the ongoing controversy on the web regarding the Protective Mothers Alliance (PMA), a grassroots advocacy organization that I helped to co-found and that is directed by Janice Levinson. I have been following the claims that have been made about PMA and about Janice; specifically, I have had the opportunity to review communications that have been shared between Janice and other individuals, and to see some of the extremely negative postings that have been made. In my opinion, the attacks that have been made on Janice and on PMA have to be called out for what they are: vicious, dishonest, threatening, and dehumanizing written assaults on a committed advocate and survivor, one who has worked tirelessly for the interests and rights of protective mothers and their children.
There are a number of sources of these attacks, but they come overwhelmingly from Claudine Dombrowski and the American Mothers Political Party (AMPP). I am not relying on Janice’s word in forming this conclusion; I have looked at many postings by Claudine and AMPP, and they are cruel, irresponsible, and outrageous. And they don’t stop; in fact, they’re getting worse over time.
Moreover, Claudine and AMPP have begun to attack a significant number of other protective mothers and their allies as well, with similar viciousness. The predictable effect of the movement’s reluctance to denounce this behavior is that it is growing and spreading.
To make sure that there is no doubt or confusion, I want to state that I give my wholehearted support to PMA and Janice Levinson. PMA has been an important and exciting development in the custody rights movement, and Janice Levinson’s work in organizing protective mothers has been excellent. I have found her to be a person of the highest integrity and commitment, combined with a deep commitment to treating participants with fairness and respect. Although she has been accused of various things, I cannot find a shred of truth to any of these accusations, and none of the accusations come from any source that I find in any way credible.
The accusations that have been made about PMA have been insulting and derisive in their tone, and have involved outright fabrications about the organization and how it works, and about Janice herself. There have also been accusations that Janice’s work is not actually associated with me, which is as bizarre as the other attacks. The attackers have used gutter language, have put up photos of Janice, and have written what can only be interpreted as threats against her. These behaviors serve to further discredit those who are making claims about PMA. These behaviors appear to come from just two or three disgruntled individuals who were angry about the appropriate requirements that the PMA structure involves, and who chose to retaliate in harmful and divisive ways.
Now for the most important part of this letter:
Claudine Dombrowski and AMPP are doing severe damage to the custody rights movement. Whatever their intentions may be, the actual effects of their actions is only to strengthen the position of the abusers. I have known of a number of individuals who have dropped out of the movement and/or who have declared that they won’t come to the BMCC anymore because they can’t stand the infighting and accusations, which are almost all traceable to the same few sources. I therefore have decided today — after viewing the latest round of unbelievable psychological assaults on Janice (see, for example, janicelevinson.blogspot.com, a blog that was created just to attack and humiliate Janice) — that I am taking the following stands:
1) I will not participate in any event or campaign that Claudine Dombrowski or AMPP are officially connected to.
2) I will not attend any event where Claudine and AMPP are present unless the organizers of the event have done everything in their power to keep them from attending.
3) I won’t work on any projects or collaborate with anyone who has worked with Claudine or AMPP in the past unless they now publicly and visibly denounce her actions.
I have waited some four years to take these steps, but now I regret that I waited so long. We cannot fight against the power and actions of abusers, and of the courts that enable them, while we remain silent and acquiescent in the face of severely abusive of treatment of our own allies.
Whatever divisiveness may result from drawing a line that places Claudine Dombrowski and AMPP outside of the custody rights movements will be far less than the divisiveness and other damage that are resulting from our failure to draw that line. So the movement needs us to take this stand.
But there is an even more important reason to take this stand, which is that it’s the right thing to do.
I ask that you not stand by quietly and allow Janice to be dragged through the mud. Please look at the attacks that have been made on her (and at the lack of any similar behavior coming from her). And then please inform everyone in your networks that you are denouncing the behavior of Claudine and the AMPP and that you do not intend to have them be part of the custody rights / protective mothers movement.
You can also help by complaining to Google about the hate-oriented website created against Janice, by going to:
https://support.google.com/blogger/answer/82111?id&url
Healing and Hope
lundybancroft.blogspot.com
Healing and Hope
lundybancroft.blogspot.com
Written by protectivemothersallianceinternational
July 31, 2013 at 10:12 pm
Posted in child abuse, children, children's rights, domestic violence, family court abuse, family court corruption, famly law
Tagged with @angelfury1212, Abusive advocates, American Mothers Political Party, AMPP, angelfury, Barry Goldstein, Battered Mothers Custody Conference, Bill Windsor, BMCC, California Protective Parents Association, Center for Judicial Excellence, child abuse, child custody, Child Protective Services, child psychology childhood trauma child expert, children, children's rights, CJE, Claudine Dombrowski, Connie Valentine, corruption, court corruption, CPPA, crime, Criminal Cyber Stalking, Cyber bullying, Cyber crimes, cyber harassment, Cyber stalking, divorce, domestic violence, domestic violence women's issues, family court, family court abuse, family court corruption, human rights, Janice Levinson, Kathleen Russell, Lawless America, Lundy Bancroft, Mo Hannah, MOLC, Mothers of Lost Children, NSCC, PMA, PMA INTERNATIONAL, Protective Mothers Alliance International, Tammy Stefano, The National Safe Child Coalition, Topeka Kansas, women's issues, women's rights